I2P (Invisible Internet Protocol) – a free tool for organizing anonymous communications via the Internet. It is a peer-to-peer network in which each user, by default, is a potential link in an anonymous chain of other network participants. I2P traffic is encrypted and cannot be analyzed. There is no concept of a “guard” node in I2P, which is present in the Tor network: there is no permanent node through which access to the network is made. User interaction with I2P on the home provider side is identified as a chaotic connection to random hosts. The number of client connections with a white IP varies on average around four thousand. In addition to the payload, this includes the exchange of service information with other network routers and transit traffic. 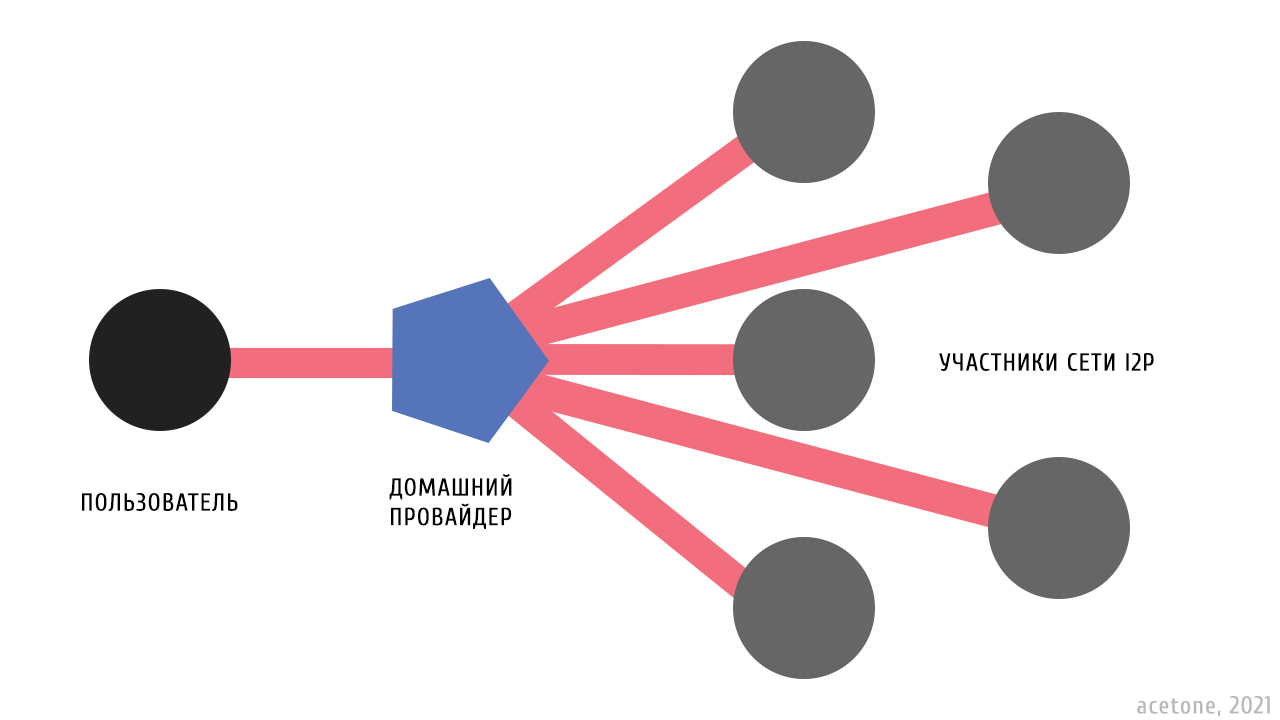
Prerequisites
A significant weak point of the I2P network is the need to contact one of the starting nodes via the regular Internet when first starting. A packet with the initial network pattern in the form of several random routers and the node that sends it are called resid. Starter nodes are maintained by enthusiasts, their list is publicly available and often undergoes changes due to ordinary human circumstances. The bottleneck lies in the ability on the provider’s side to identify most calls to the resid through monitoring DNS queries, as well as in blocking the domains of the starting nodes, which will make the first launch difficult for an inexperienced user, because will require the use of a proxy or VPN.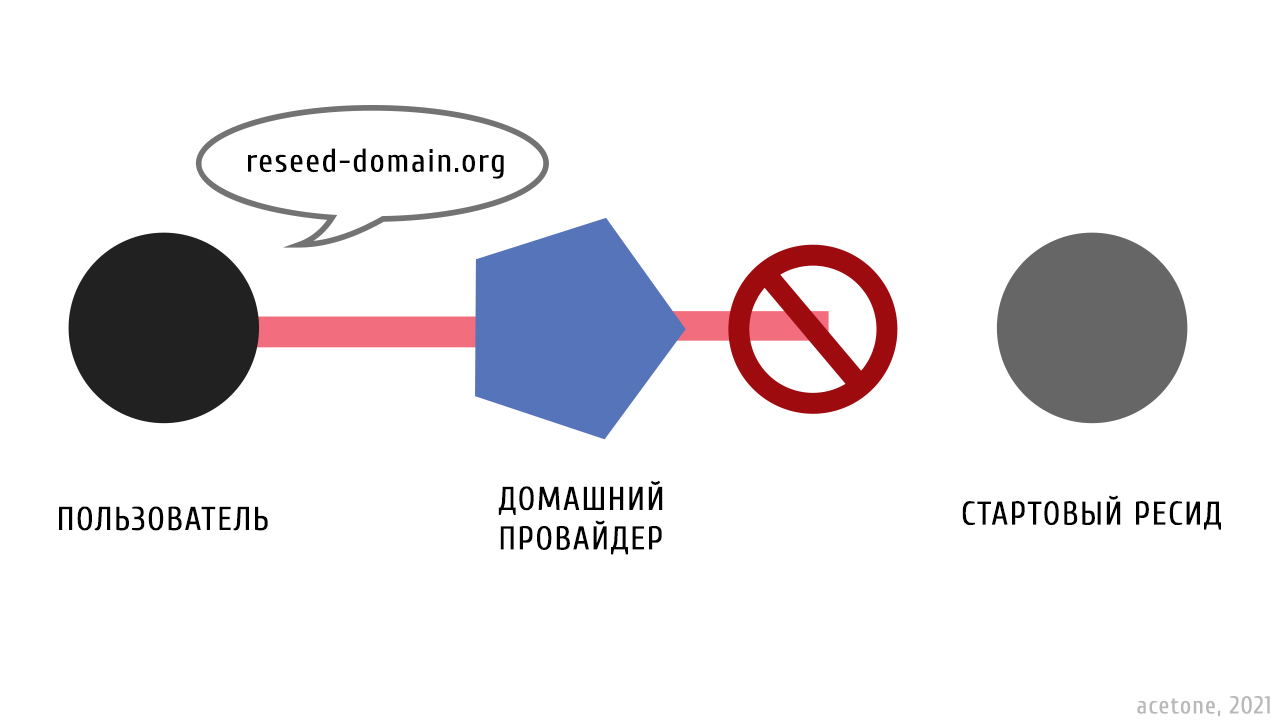
Unlike the regular Internet, I2P users without a dedicated address have a worse quality of using the hidden network than subscribers with a white IP. This is due to the constant need for direct communication with other routers on the network. Each router publishes its address, which includes encryption keys, an IP address, and a port for receiving messages. Obviously, reaching a network host behind a NAT server is not an easy task. 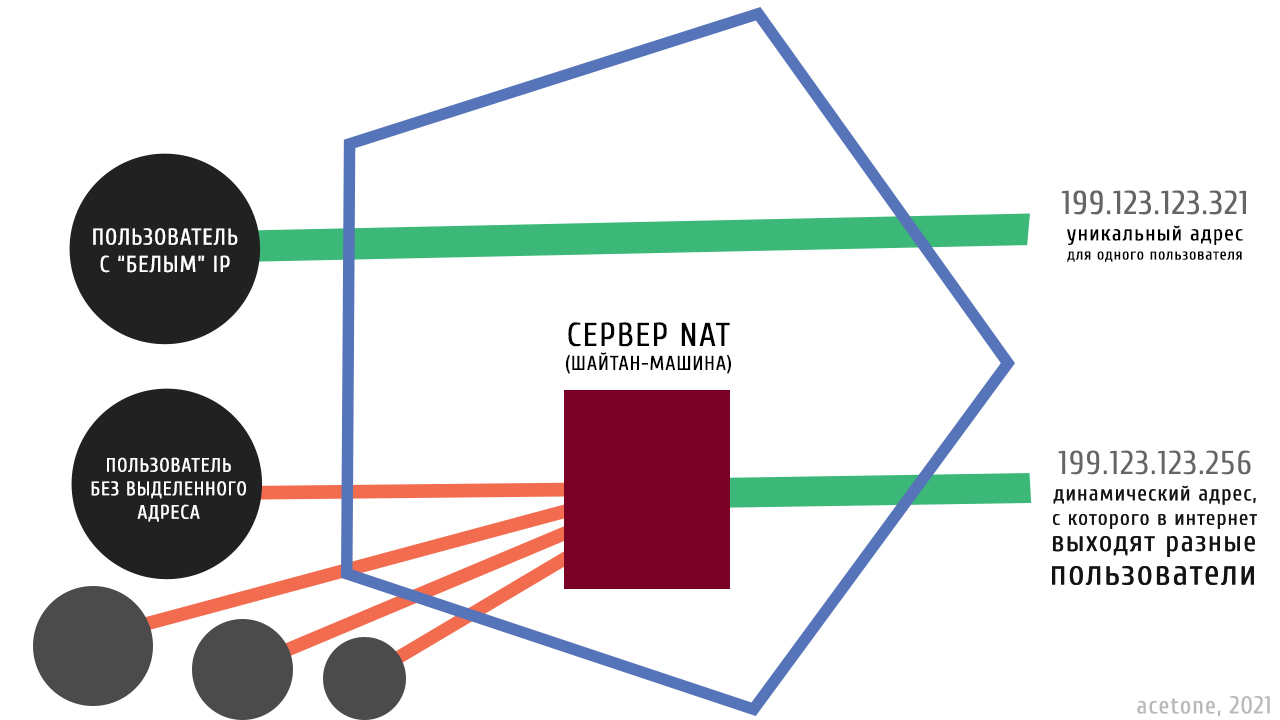
However, the operation of routers without a dedicated address is possible: a client of a network behind NAT has to constantly maintain an active UDP connection, reserving a port on the provider’s output server, to which calls will be transferred to the client. This scenario is very complicated, especially when it comes to initializing a connection from the outside. The mechanics of client operation behind NAT is a work of engineering that deserves a separate article.
Briefly about Yggdrasil
Yggdrasil Network – one of the few functional mesh network protocols. The main concept is automatic routing in the internal IPv6 subnet (200::/7) and absolute scalability. Yggdrasil is a completely peer-to-peer network: there are no “master nodes” to which any global responsibility is delegated. Is an ideological continuation of the CJDNS (Hyperboria) project).
The abstract idea of a mesh network puts performance, privacy and ease of use at the forefront: traffic encryption and a low barrier to entry for new users. Yggdrasil is not an anonymity tool, because... The nodes closest to the user see his real network interfaces on the local network, or the IP address when connecting to a public peer via the Internet. Mesh networks are used in organizing pseudo-local networks, connecting remote computers into one IPv6 network (similar to Hamachi for playing Minecraft and other multiplayer games). Also serves for organizing other intranet resources such as websites and VoIP telephony.
First attempts at integration
Details
A small note
Описанные ниже нововведения на момент публикации касаются только i2pd – I2P-роутера на C++. Клиент Yggdrasil на устройство устанавливается отдельно.
The I2P router publishes its addresses, including IPv6, if it is enabled in the config and is actually available. Since Yggdrasil does not provide the user with a local proxy, but with a full-fledged network interface (using the TUN driver from WireGuard), until recently, an I2P router published an IPv6 address from the Yggdrasil subnet. Since there were more than one or even two users with the IPv6 protocol enabled in the I2P router configuration and Yggdrasil installed, it was periodically possible to see that the I2P client (router) communicated with other Yggdrasil addresses.
However, the following disadvantages are evident::
access to the resid should ultimately be carried out via the regular Internet;
The IPv6-Yggdrasil address published by the router is unknown and inaccessible for the vast majority of I2P users;
successful launch of an I2P router on a Yggdrasil-Only device is unlikely due to the possible absence of nodes with an IPv6-Yggdrasil address in the router's resid or local database.
The beginning of full compatibility
From version 2.36.0 i2pd has several new configuration parameters, the main one of which is meshnets.yggdrasil=true. This setting is independent of IPv4 and IPv6 configuration. In particular, real network interfaces may be disabled. In this case, the I2P router will operate in Yggdrasil-Only mode.
A special resid has also been organized, accessible from Yggdrasil and giving the user a package primarily consisting of well-known routers with an IPv6-Yggdrasil address. Every time you start an I2P router operating in Yggdrasil-Only mode, the local database is checked for available nodes at the transport level, i.e. presence of other nodes with IPv6-Yggdrasil. If for some reason there are no compatible routers in the local database, the Yggdrasil resource is contacted again.
With modern use of Yggdrasil, mostly through overlay connections to public peers via the Internet, the operation of an I2P router in Yggdrasil is comparable to a “Tor-over-VPN” combination: this approach completely hides the fact of using a hidden network from the home provider. In the case of I2P, there is another specific advantage: the user does not need to have a dedicated IP from the provider for trouble-free external calls, because IPv6-Yggdrasil is globally available within the Yggdrasil network segment (a physically connected group of participants, including through public peers on the Internet).
Network integrity
The described solution is not a factor in I2P fragmentation. Building hidden network tunnels is a very intensive and even sophisticated process, which also involves coordinating the transport capabilities of the nodes. By forming a “garlic” - an encrypted message to a group of nodes that should form a tunnel - the router checks their addresses for compatibility. For example, a node with a single IPv4 address will not be instructed to contact an IPv6 address because this is obviously impossible.
In order for a Yggdrasil-Only router to build a tunnel to a node with an address from the regular Internet, at a minimum a transit router will be selected that has two interfaces: IPv6-Yggdrasil and, for example, regular IPv4. In turn, other Yggdrasil-Only routers can also act as transit links in the tunnel, but only for communication with nodes compatible in transport, i.e. also having the Yggdrasil network interface. The greater the number of routers in an I2P network with simultaneously enabled IPv4, IPv6 and Yggdrasil interfaces, the more connected the network.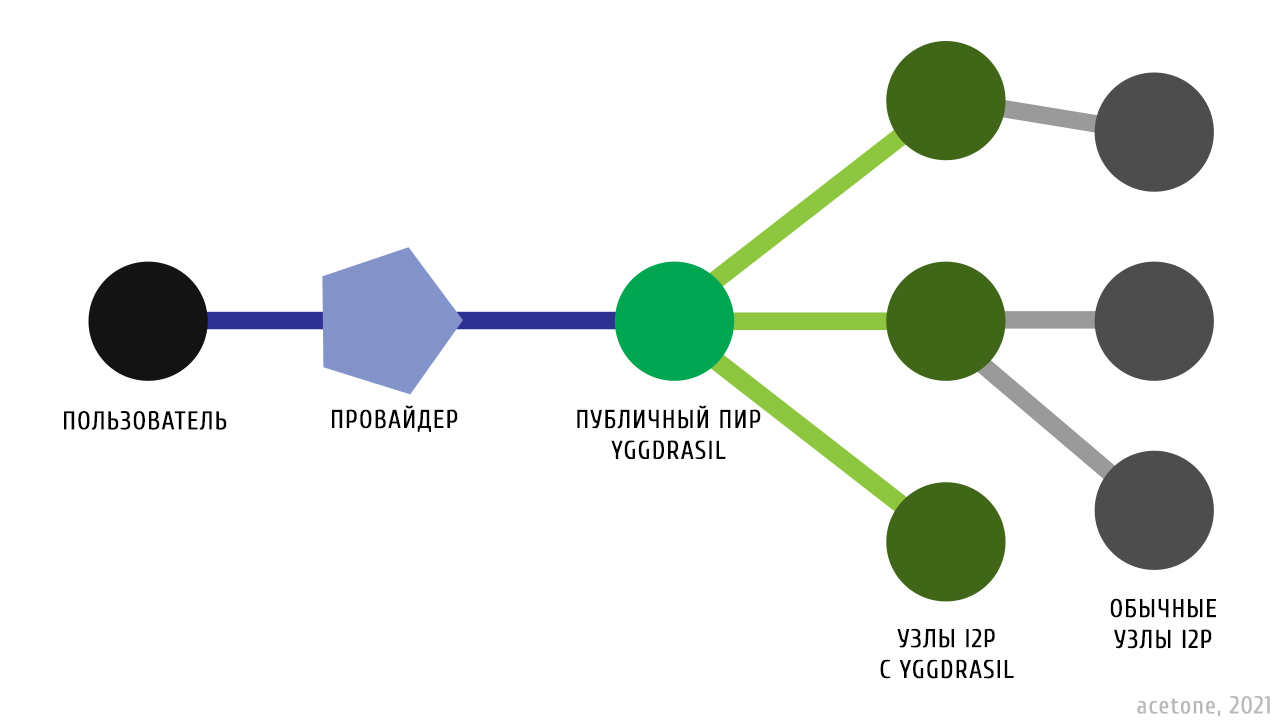
Perspective
The example with Yggdrasil is a partial step into the future, and not an end in itself. The described experience of successfully integrating a hidden network into a mesh network is an important conceptual step that, if necessary, will allow the I2P network to be integrated into other mesh networks. The prospect opens up when considering self-organized mesh network segments, for example, in apartment buildings without a centralized provider. In the local network, the Yggdrasil client automatically finds other nodes and communicates with them, acting as a transit node if necessary. When at least one node in such a segment is connected to another network segment (for example, to a global one via the Internet), the networks are automatically united. This approach to organizing a network has become even more realistic, because Now there is a second side of the usual Internet - hidden.
For a more detailed acquaintance with the mentioned technologies, I recommend the articles: about I2P And about Yggdrasil.
